So passwordless authentication is something pretty awesome – It removes the need for users to know their own password because you can replace the password with a multifactor authentication prompt. Microsoft has taken Passwordless out of preview after about 2 years. Microsoft’s implementation of passwordless prompts the user to click the right number on their screen. This also prevents users from just hitting on “OK” for random push prompts, so again a little bit of extra safety.
We really like using Passwordless at our MSP and for our clients, we often combine Passwordless with FIDO keys or with other forms of Conditional Access and Multi Factor authentication. Deploying passwordless in all your tenants can be done with executing the script below. This doesn’t really make any changes for users yet, as they have to register for passwordless themselves.
The Script
######### Secrets #########
$ApplicationId = 'YourAPPID'
$ApplicationSecret = 'YourAppPassword' | Convertto-SecureString -AsPlainText -Force
$TenantID = 'YourTenantID'
$RefreshToken = 'Refreshtoken'
$UPN = "Valid-upn"
######### Secrets #########
$credential = New-Object System.Management.Automation.PSCredential($ApplicationId, $ApplicationSecret)
$aadGraphToken = New-PartnerAccessToken -ApplicationId $ApplicationId -Credential $credential -RefreshToken $refreshToken -Scopes 'https://graph.windows.net/.default' -ServicePrincipal -Tenant $tenantID
$graphToken = New-PartnerAccessToken -ApplicationId $ApplicationId -Credential $credential -RefreshToken $refreshToken -Scopes 'https://graph.microsoft.com/.default' -ServicePrincipal -Tenant $tenantID
Install-module AzureADPreview -AllowClobber
import-module AzureADPreview
Connect-AzureAD -AadAccessToken $aadGraphToken.AccessToken -AccountId $upn -MsAccessToken $graphToken.AccessToken -TenantId $tenantID | Out-Null
$tenants = Get-AzureAdContract -All:$true
Disconnect-AzureAD
foreach ($tenant in $tenants) {
write-host "Working on client $($tenant.defaultdomainname)"
try {
$CustAadGraphToken = New-PartnerAccessToken -ApplicationId $ApplicationId -Credential $credential -RefreshToken $refreshToken -Scopes "https://graph.windows.net/.default" -ServicePrincipal -Tenant $tenant.CustomerContextId
$CustGraphToken = New-PartnerAccessToken -ApplicationId $ApplicationId -Credential $credential -RefreshToken $refreshToken -Scopes "https://graph.microsoft.com/.default" -ServicePrincipal -Tenant $tenant.CustomerContextId
Connect-AzureAD -AadAccessToken $CustAadGraphToken.AccessToken -AccountId $upn -MsAccessToken $CustGraphToken.AccessToken -TenantId $tenant.CustomerContextId | out-null
$exists = Get-AzureADPolicy | Where-Object -Property type -eq AuthenticatorAppSignInPolicy
if ($exists) { write-host "Policy exists for $($tenant.DefaultDomainName)"; continue }
New-AzureADPolicy -Type AuthenticatorAppSignInPolicy -Definition '{"AuthenticatorAppSignInPolicy":{"Enabled":true}}' -isOrganizationDefault $true -DisplayName 'PasswordlessSignin'
}
catch {
Write-Warning "Could not log into tenant $($tenant.DefaultDomainName) or retrieve policy. Error: $($_.Exception.Message)"
}
}
Now, that’s the scripting part, lets move over to the user part.
User Setup
The user still has to perform some tasks themselves if they want to use passwordless. First off, the user has to be registered for Multi-factor authentication already, using the Microsoft Authenticator app. If they are not, have them do that.
When the user is completely registered, have them open the application and click on their username, then click on “Enable Phone Signin” – From that moment forward, the user will no longer be prompted for their password, but get the following pop-up
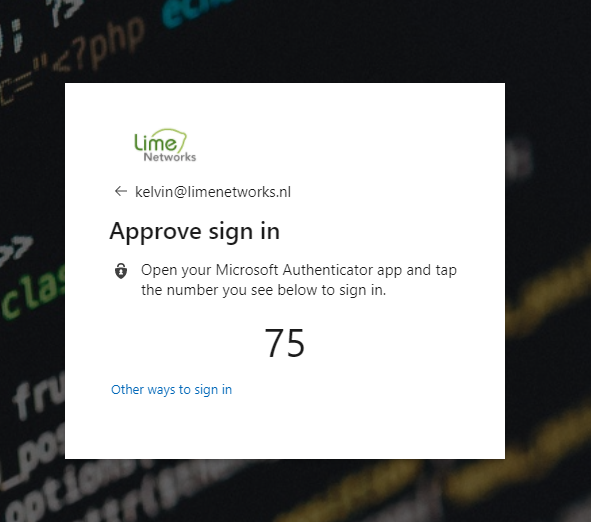
And that’s it! as always, Happy PowerShelling.