I’m a big fan of Dell’s Command Update utility. Dell Command update is a program that makes updating Dell based devices super easy, a single utility that you can install on any workstation to update all devices is great. We always deploy Dell Command update with any machine we hand out to clients.
The next issue that occurs is that we need to know if the updates are running well. For this, I’ve made a monitoring set. To make sure that you don’t just monitor without action, we also created a set that automatically remediates.
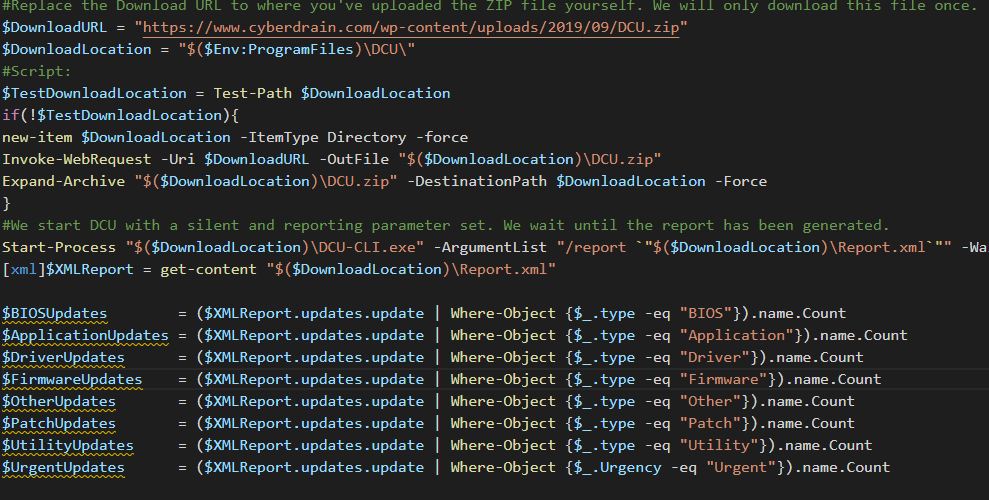
The monitoring script
The monitoring script downloads a zip file with the Dell Command Update utility. You can create this zip-file yourself by installing Dell Command Update and simply zipping the install location. It then unzips the downloaded file, and runs the DCU-cli with the Report Parameter, I would advise to only run this set on an hourly or even daily schedule, using your RMM system of course.
|
|
As this is a number monitor, if something is 0 you are completely up to date, we monitor all type of updates. We also like knowing if an update is urgent, which has a separate category.
Remediation
So remediation can be done quickly, In theory we would only have to run a single command, which is the following script
|
|
The problem with running this script directly that by default all updates that the DCU finds will be installed, and you cannot set a classification to be excluded. If you would like to exclude specific update types such as BIOS updates or utility software, you’ll have to do this:
- Open DCU on your administrator workstation
- click on the cog in the top right corner
- update filter:, unselect the updates you want to exclude.
- Export/Import: and export the MySettings.xml file.
- Add this MySettings.xml file to your self-hosted DCU zip file.
If you’ve done this small list of tasks, then use the following script to install the updates instead:
|
|
When executing Thunderbolt or BIOS updates. You will also need to suspend Bitlocker. You can use the following script for this. My advice would be to execute the reboot immediately in this case – and only use this if you are certain that the device is in a secure environment during execution.
|
|
the AMP file can be found here. As always, Happy PowerShelling!