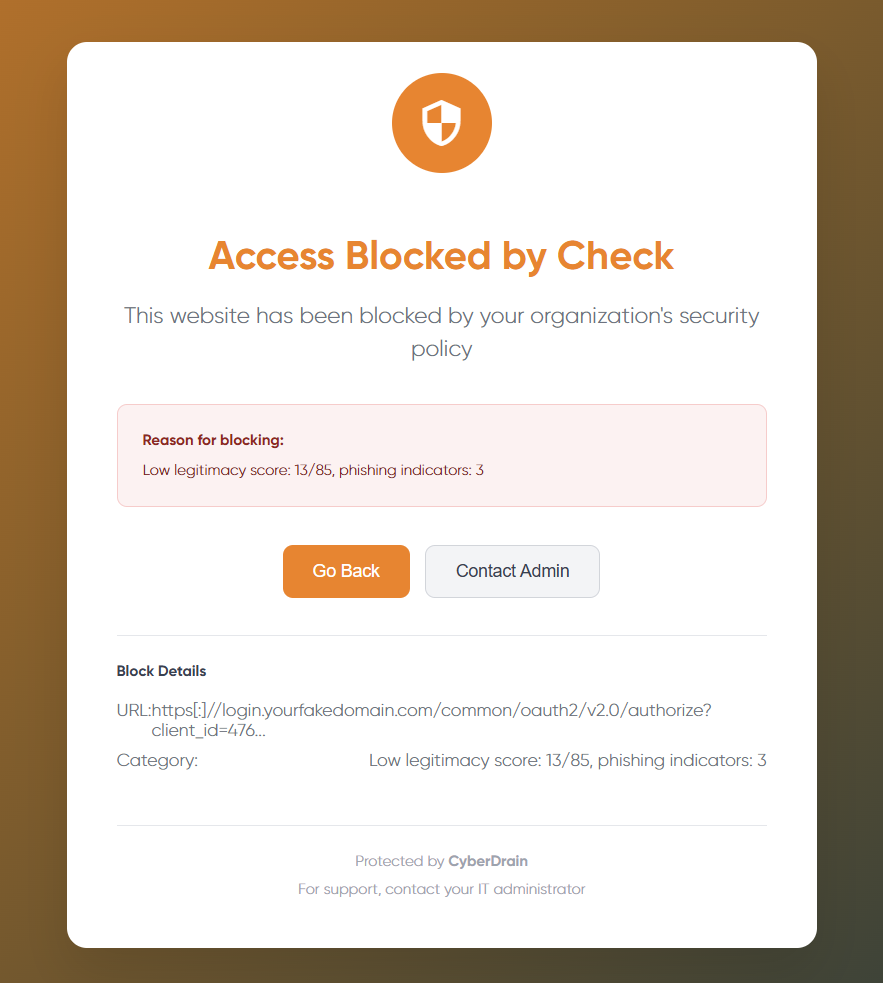
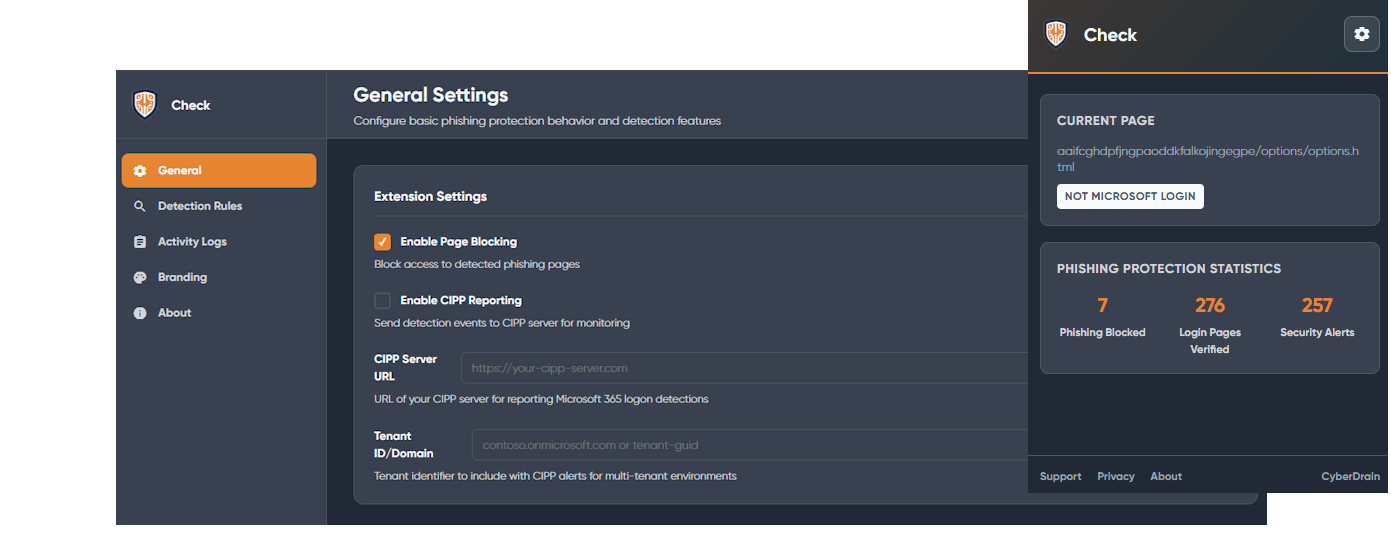
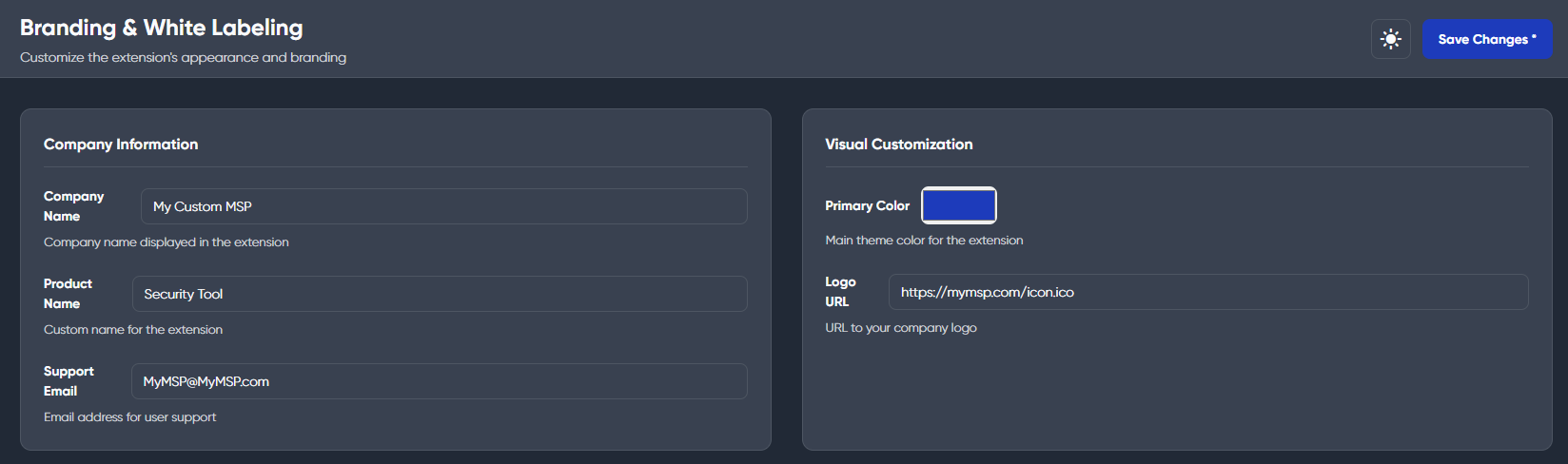
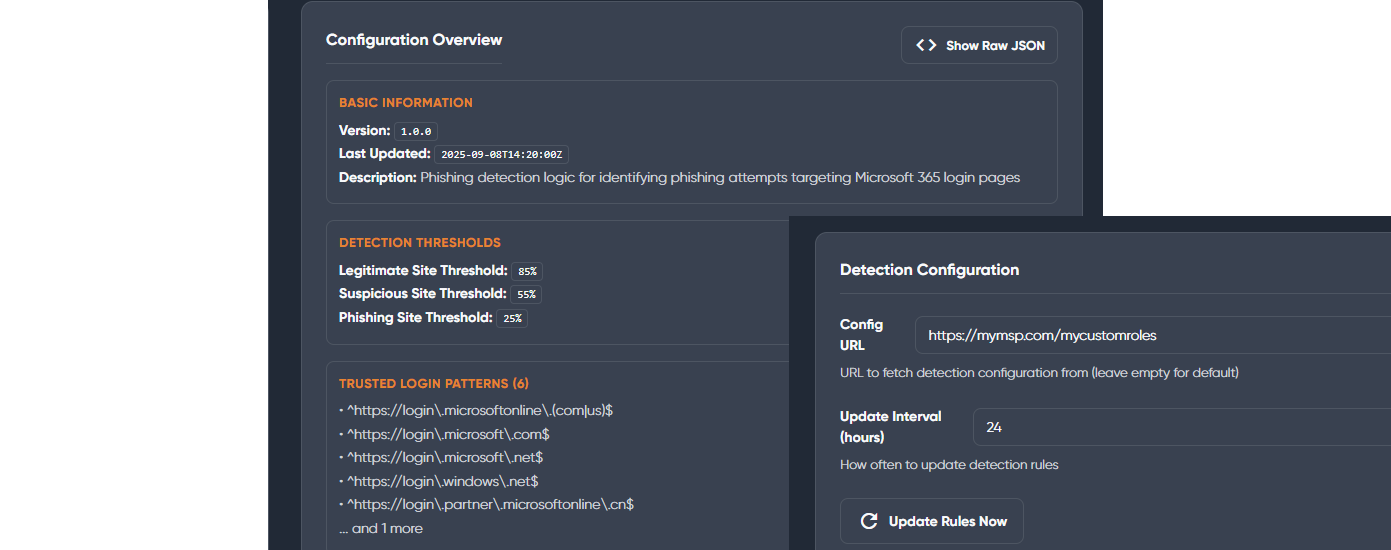
Stop Phishing Attacks Before the Breach
Check blocks malicious pages at the browser level, preventing credential theft where email filters fail. Each successful phishing attack costs MSPs 2-3 hours of incident response. Check prevents these incidents.
Join the development community contributing to Check.