Today Greynoise released a community edition of their API, I saw this flying by on Twitter and immediately decided to blog about it. I love it when vendors make major data points available for everyone, especially when the data could be super useful in security investigations.
I’ve decided to make a blog on how you can monitor the IP reputation of all remote connections to a machine. You can then use this data to either block specific IP addresses, or add them to your filters so your SIEM or logging solution doesn’t get clogged up with useless information.
The script has a couple of other use cases too, It seems that Greynoise API also shows if the IP has a bad reputation or not. You can use the script below to automatically add all malicious IPs to your firewall, that way you’ll have a little bit of extra security against those pesky scanning and spamming IPs.
Of course this can be achieved with any other tool too, but I really like that Greynoise is opening up a bit more of community data, this can improve us all.
The script
You can run the script using your RMM system, as with most of my blogs. You can add any invalid IP to the list too, in case it’s required.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
|
$APIUrl = "https://api.greynoise.io/v3/community/"
$InvalidIPs = "::", "0.0.0.0", "127.0.0.1"
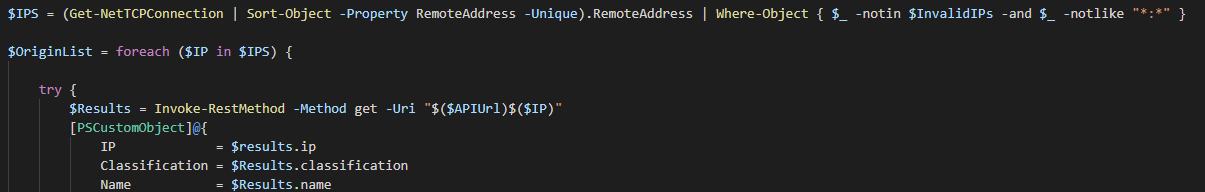
$IPS = (Get-NetTCPConnection | Sort-Object -Property RemoteAddress -Unique).RemoteAddress | Where-Object { $_ -notin $InvalidIPs -and $_ -notlike "_:_" }
$OriginList = foreach ($IP in $IPS) {
try {
$Results = Invoke-RestMethod -Method get -Uri "$($APIUrl)$($IP)"
[PSCustomObject]@{
IP = $results.ip
Classification = $Results.classification
Name = $Results.name
GreynoiseLink = $Results.link
Noise = $results.noise
Message = $Results.message
Error = $null
}
}
catch {
[PSCustomObject]@{
IP = $ip
Classification = 'Unknown'
Name = 'Unknown'
GreynoiseLink = 'No link available'
Noise = 'Unknown'
Message = $_.Exception.Response.StatusDescription
Error = $_.Exception.Response.StatusCode.value__
}
}
}
$BadResults = $OriginList | where-object { $_.Error -eq $null -and $_.Classification -ne 'benign' -and $\_.Noise -ne $false }
if ($BadResults) {
Write-host "Warning: Results with non-benign results found. Investigate immediately and block if required."
$BadResults
}
else {
write-host "No non-benign results found."
$OriginList
}
|
And that’s it. As always, Happy PowerShelling!