So let’s start with the great news first; PowerShell protect is now open-source and free to use! PowerShell Protect is a AMSI Provider for PowerShell, now technically this sounds rather complex but it pretty much means that PowerShell Protect is able to secure the PowerShell host in the same way your antivirus does.
The great thing about PowerShell Protect is that it allows you to monitor exactly which commands have been executed, but also catch them and block them for usage if you don’t trust it.
This means you can block so called LoLBas and LolBin via Powershell with relative ease. In this blog I’ll show you to do deploy PowerShell Protect, and how to monitor activity generated by it. So let’s start getting our clients more secure and less prone to persistence attacks.
Installing PowerShell Protect
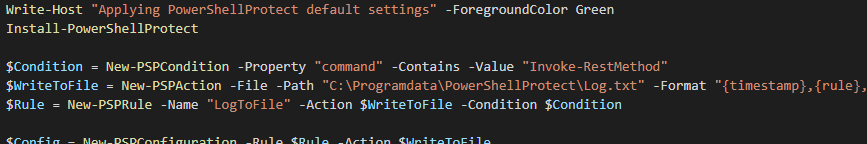
Installing PowerShell Protect is done from the PowerShell gallery, the moment you install the module nothing happens yet, and you’ll need to add rules and install the actual AMSI provider. We’re using the default rules, but are also adding some rules for logging entries we want to see, as an example I’ll add logging for invoke-restmethod
This means we’ll block the following list;
- Block AMSI Bypass Protection
- Block Module and Script Block Logging Bypass Protection
- Block Assembly Load from Memory
- Block Disabling Defender
- Block Use of the System.Reflection.Emit Namespace
- Block PowerSploit(Invoke-mimikatz and derivatives.)
- Block the Marshal Class
- Block WMI Event Subscription persistance
- Block Bloodhound
- Block Kerberoasting
- Block invoke-expression
All of these rules heighten our protection against bad actors, while still allowing enough flexibility to actually use PowerShell for our day to day operations with our RMM system, so let’s deploy shall we?
|
|
So now all invoke-restmethod requests are logged to C:\Programdata\PowershellProtect\Log.txt, and all those things up there get blocked by PowerShell too! Let’s move on to a bit of monitoring:
Monitoring the PowerShell Protect log
Because we’re outputting the log in a CSV form, it becomes easy to monitor in PowerShell, we load the file as a CSV and filter only events that happened in the last 5 minutes.
|
|
So this outputs if there are no events found, or when there are events it’ll output exactly what was found, the time and date, which executable ran the script and to top it off which user executed the command.
And that’s it! there’s a lot more to PowerShell protect and I’ll probably make a second blog about it soon, right after I assist the project with some changes 😉
As always, Happy PowerShelling!