A bunch of bad actors these days uses the great psexec tool by Sysinternals/Microsoft to try to move through the network latterly. PSExec allows you to remotely execute commands on different computers through a very simple command line interface. PSexec also allows you to execute commands or scripts as the SYSTEM account.
We use PSExec professionally to run specific tooling that requires the highest privileges, this means that just flat out blocking PSExec execution on our networks is not possible. We do want to know whenever people do execute this, so we can use it as an early warning system. Please note that this does not capture PSexec clones such as CDEXec and PAexec.
Grabbing PSExec usage actually did not look that hard – you either look for the service it creates, or for the currently running file, so the following simple script would solve it I thought.
The Scripts
|
|
But after checking some of my older scripts I’ve actually found the -r option for PSExec. The -R parameter allows you to change both the servicename and the executable name, making it a little harder to find now. To solve this, we can look for the specific executable where the description is set to PSExec.
|
|
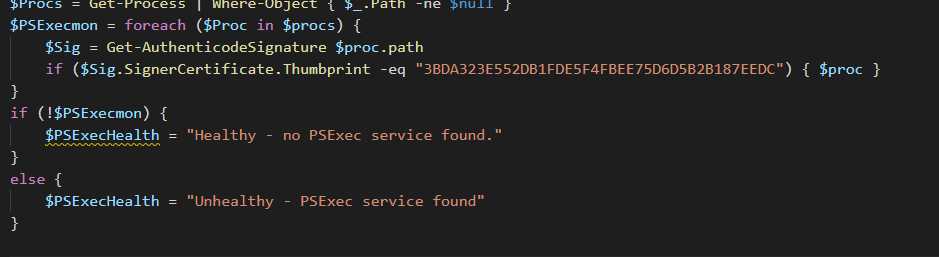
But now you’re saying “But Kelvin, what is someone removes the personal identifying properties?! You won’t find it but it will still run.” And I’d say you’re absolutely right about that. So let’s try a third option;
|
|
This last option does have a downside too; Microsoft used the same signing certificate for the PSTools as they did for a .NET installer. This might generate one or two false positives, but it does seem the best way to detect PsExec usage right now. We’ve loaded this up in our RMM and are running this job to make sure we can see whenever PSExec is executed. With this option you could also stop the process automatically.
And that’s it! Hopefully it helps prevent lateral movement in your networks too. As always, Happy PowerShelling!