Hi All,
My next couple of blogs will be a series of blogs where I will be explaining on how to use PowerShell for the monitoring of critical infrastructure. I will be releasing a blog every day that will touch on how to monitor specific software components, but also network devices from Ubiquity, third-party API’s and Office365. I will also be showing how you can integrate this monitoring in current RMM packages such as Solarwinds N-Central, Solarwinds RMM MSP and even include the required files to import the monitoring set directly into your system.
Requirements:
- Ubiquity Unifi Controller running 5.x.
- Read-only user on all sites.
- PowerShell v3 or higher
Creating the monitoring sets:
Before we start, credit where credit is due: Most of this post is based on the code found on this reddit post. Connecting to the Unifi controller via the API is completely based on that post and I’ve only modified a few small parts to make connecting easier, I also want to make sure you understand what we’re doing here; We will be using the REST API to query the controller for information, not the access points, switches, or routers themselves. Now that we’re clear lets dive straight into it and start maintaining our unifi devices by using PowerShell.
This blog post relates to the previous blog found here. There will be no monitoring sets included as this blog is more about maintenance jobs than device management and monitoring. You can run this script from the any RMM package using schedulded tasks, of by using an Azure Function as described here.
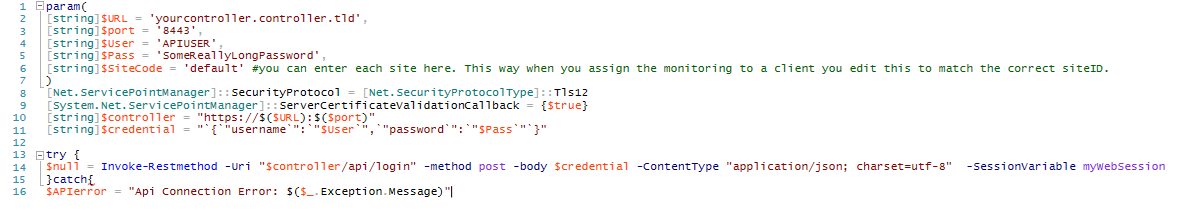
Lets get into the scripting part of maintaining our devices, First we’ll have to connect to the API as before:
|
|
After connecting to the API we’re going to use a loop to check all the devices that require and upgrade, and send the upgrade command to them. Before moving on, make sure you are connected to the API by querying $APIError.
Upgrade all devices in the selected site($SiteID) that require upgrade:
|
|
If you’re having alot of sites and agreed on a single maintenance cycle for all your client base, you can use the script below instead. This upgrades all sites and all devices to the latest version available on the controller.
Upgrade all devices in all sites that require upgrade:
|
|
And that’s it! using these scripts you can automate any firmware upgrades to only occur when you want them too and without interrupting the user experience.